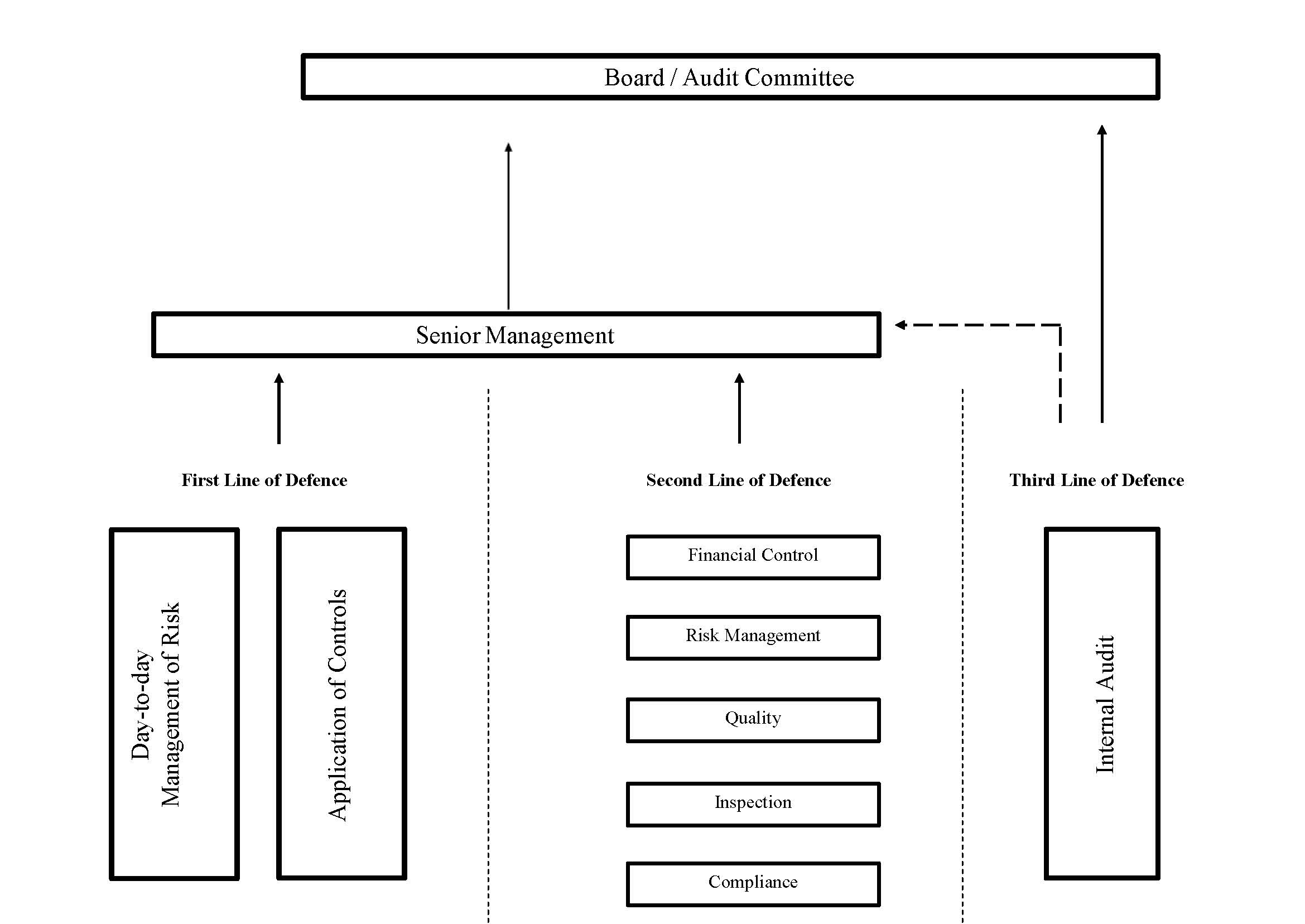
Three Lines of Defence
Recently I read a DevOps book Investments Unlimited, a story about automating IT governance. It is more of a fictional novel than its thought-provoking predecessors (The Phoenix Project and The Unicorn Project). The story applied the Three Lines of Defence (3LoD) framework for IT processes governance, and concluded with continuous reporting of process compliance.
The Three Lines of Defence
TIL - The Chartered Institute of Internal Auditors (IIA) position the 3LoDs framework as effective management of risk with three lines approach. In laymen’s term, they are:
- Governance operations
- Governance management
- Governance oversight (governance of governance)
Below is the official diagram from IIA position paper.
Source: © Chartered Institute of Internal Auditors, March 2015
Increase IT governance velocity
3LoDs is a great approach, and I have seen some of my clients applying it vigorously with well-documented processes and procedures. But they quickly become the bottlenecks that limit the delivery velocity.
The classic road humps I encountered are security review assessment, architecture review, and budget approval. They are valuable adding activities (not waste), and usually increase lead times due to discovery of unplanned works or remediation of unfinished work.
It is possible to remove or reduce these humps reduce friction and get faster feedback.
graph LR
A[Board / Audit Committee] --- B[IT Management]
subgraph 1LoD
C(Day-to-day operations)
D(Apply controls in design)
E(Apply controls in delivery)
end
B --- 1LoD
subgraph 2LoD
G[Financial Management]
H[Risk Management]
I[Architecture Fitness]
J[Security & Data Compliance]
end
B --- 2LoD
subgraph 3LoD
L[Internal Audit]
M[Independent Assessors]
end
A --- 3LoD
B -.- 3LoD
IT Management
- Interpret legislative and regulatory requirements for corporate governance policies
- Translate corporate governance policies into IT governance guardrails
- Publish referenced architectures and guidelines that align to the guardrails (with vendors consultation)
First Line of Defence (1LoD)
- Implement and inner-source referenced architectures as
- repository template with compliant workflows
- as-code templates
- starter workflow
- reusuable workflow
- required workflow
- reusable packages
- Deliver services with these shared components (as much as it makes sense)
- Continuous monitor for configuration drifts and response to alerts
- safe-settings
Second Line of Defence (2LoD)
- Implement IT governance guardrails as-code, continuous monitor for non-compliance, and remediate
- protectware - protect npm packages from malware
- Continuous evaluation of interpreted guardrails and referenced controls (many of these interpretations are moving to outcomes-based, rather looking for particular configuration outputs)
- Continuous alignment of referenced architectures and guidelines to desired outcomes and vendor innovations
- Monitoring the SLOs of identified risks to assure the risks are addressed
Third Line of Defence (3LoD)
- Monitor spikes and abnormalities in reportings
- Assure 1LoD and 2LoD are operating effectively and advise any improvement area to both Board and IT Management.